The ultimate aim of the project is to secure a tablet application that is used in the financial sector for transactions. This project will encounter the various security issues faced by mobile devices and attempts to provide one or more solutions to the threats. The project was initiated with the investigation of threats that could attack the tablet application. Though the evolution in technology has made many things possible, the most profound architectural challenge lies in the security of the system. It also puts the solutions into practice and displays a secure application for portfolio managers. The secure application will be encapsulated with different layers of security, so that even if the device is lost, the user can still secure his data from being used by unwanted users. The project on a whole looks at the security from developer and end user perspectives.
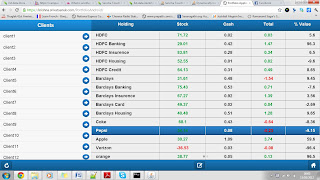 |
| Application running on Android |
 |
| Application running on Android |
 |
| Login error from OpenAM |
 |
| Logout screen confirms to save |
 |
| Same Application on IOS IPAD |
The project begins with the analysis of various threats that could affect a tablet-based application. It mainly deals with storing a data securely in a tablet device, securing the inter process communications & avoid hacking its data by other applications. It also deals with the secure server interactions. The project also secures the “intent” messages & broadcast signals to avoid the hacking data by other applications. It ensures that even when the device is jail-broken (A jail-broken phone can be used with any service provider or can be updated independently from the device manufacturer) the person should have a password, to decrypt the data from the device. The user identity and access will be validated by an identity management server and authorized before they log on to the corporate server. The portfolio application will fetch the data from a JSON servlet and displays it on the tablet. So the project required that server communication be secured with SSL/TLS by authenticating both server and client using certificates. The data transferred will be done using JSON objects. Normally applications use 1-way SSL where the client usually verifies the server, however in this scenario a 2-way SSL encryption is used where both client and server verify each other. The application is restricted to communicate only with specific web servers. On top of all the above mentioned security, the application will connect via Virtual Private networks (VPN) based connectivity to the corporate network along with split tunneling, which ensures the best security for the project.

No comments:
Post a Comment