The one time password usually generated with a RSA token
device or nowadays it got developed with an application in a mobile that
produces the one time password for the tier 2 authentication. The user login
requires the token password which the RSA produces, but the users are forced to
have the device with them always when they need to login. Once the token
produces a password it cannot be reused. OpenAM offers a ready to use OTP based
on authentication module to deliver the password via email or a text SMS.
OpenAM ensures a hashed message authentication. The HOTP authentication module
is configured to work as part of an authentication chain that includes a first
factor authentication (Usual login credentials Username and password).The HOTP
requires at least one authentication done before it delivers the OTP.
Steps to configure HOTP
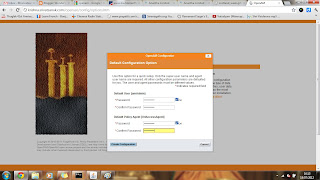
- Login to OpenAM Administrator console ->Access Control tab ->Realm->Authentication. Then Click on Module Instances ->New to create a Module instance. Assign a name to the HOTP. (HOTP)
- Configure the HOTP authentication module properties.
- Configure the authentication chain that includes HOTP authentication module.HOTP cannot be a primary(first ) authentication module.
- Since it cannot validate the User with his credentials. To create an authentication chain goto the openam admin console select Access Control ->Authentication Chaining.Click New Assign a name and choose HOTP- module instance Required
- Now the HOTP configuration is completed. Then create a user profile and add the details then for the telephone number. For a complete list of Email to SMS Gateways refer to:http://www.mutube.com/projects/open-email-to-sms/gateway-list/
-
Test drive the configured One-time Password based OpenAM authentication, by accessing the URL of the configured “Two-factor” authentication chain as follows:

Configuring HOTP authentication

Making HOTP as Authentication chain